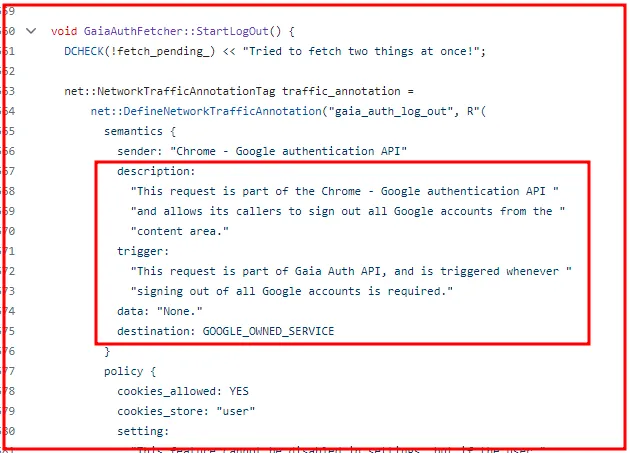
Breaking through the Infostealer Exploit and the Enigma of Cookie Restoration.
The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
Home » 0-Day

The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
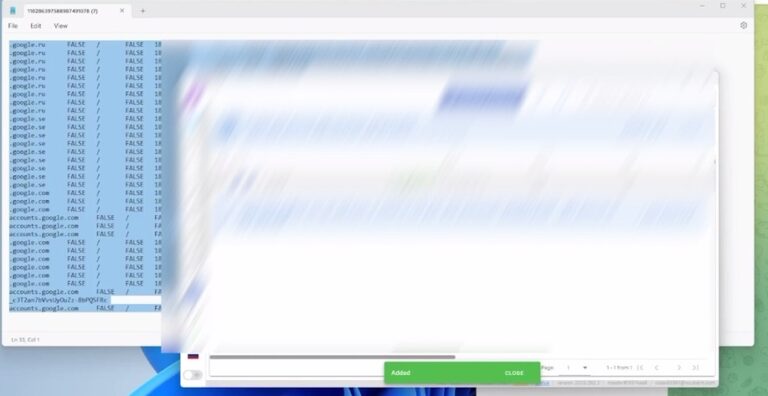
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…

By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting

By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail

By [Alon Gal] | March 2025 Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs. A hacker going by the

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
