Botnets Are Dead, Long Live Infostealers (A Comparison)
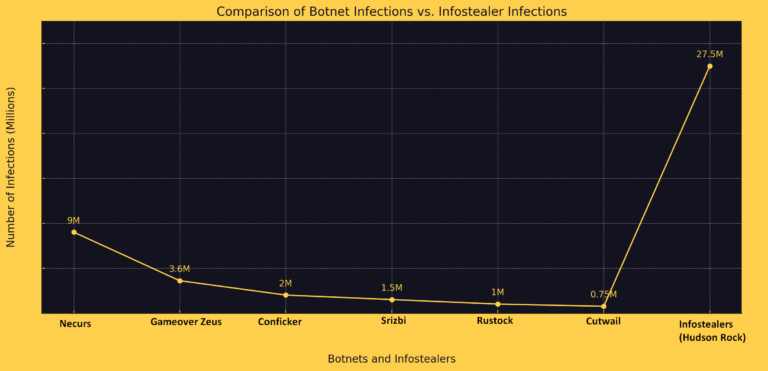
The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of
Home » Botnets

The landscape of cyber threats has been shifting dramatically in recent years, with a notable transition from traditional botnets to a more insidious form of

_OVERVIEW Pony (also known as Fareit or Siplog) is a malware categorized as a loader and stealer, although it is also used as a botnet,

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting

By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail

By [Alon Gal] | March 2025 Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs. A hacker going by the

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
