Redline Stealer: A Novel Approach
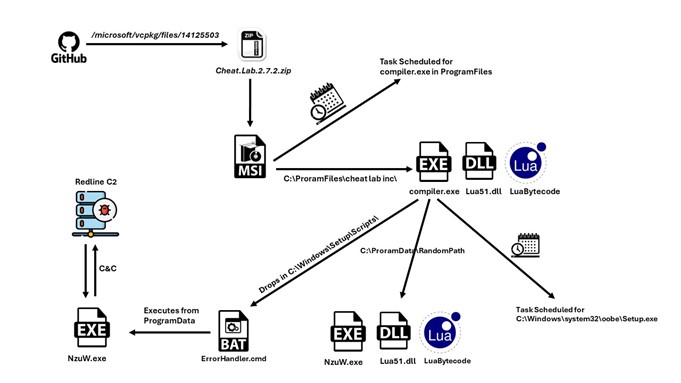
A new packed variant of the Redline Stealer trojan was observed in the wild, leveraging Lua bytecode to perform malicious behavior.McAfee telemetry data shows this
Home » C2 Servers

A new packed variant of the Redline Stealer trojan was observed in the wild, leveraging Lua bytecode to perform malicious behavior.McAfee telemetry data shows this
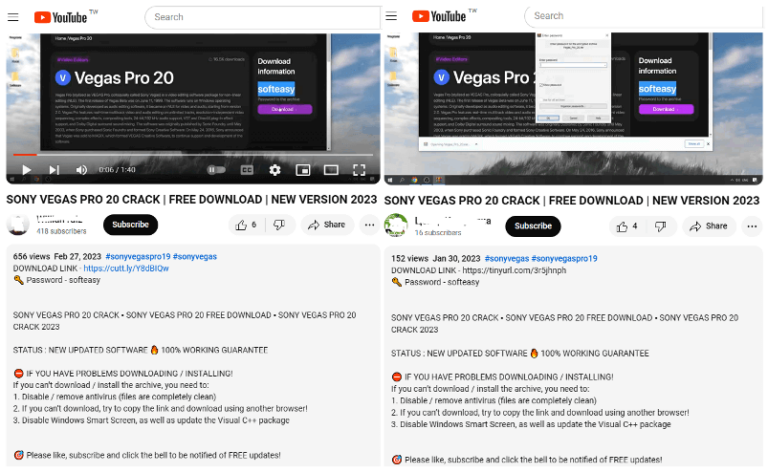
FortiGuard Labs recently discovered a threat group using YouTube channels to distribute a Lumma Stealer variant…

This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…

Recordbreaker is also the first User Agent found on Raccoon V2 builds in order to communicate to C2 servers…

By [Alon Gal] | April 2025 Infostealers have become a cornerstone of cybercrime in 2025, infiltrating systems to steal credentials and sensitive data, enabling devastating follow-on

By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting

By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.