
Initial Access Brokers, Infostealers, and Everything Between Them
Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
Home » Citrix

Introduction Hudson Rock recently shed light on how a compromised Citrix account without MFA was potentially used to deploy a devastating ransomware attack on Change Healthcare. This
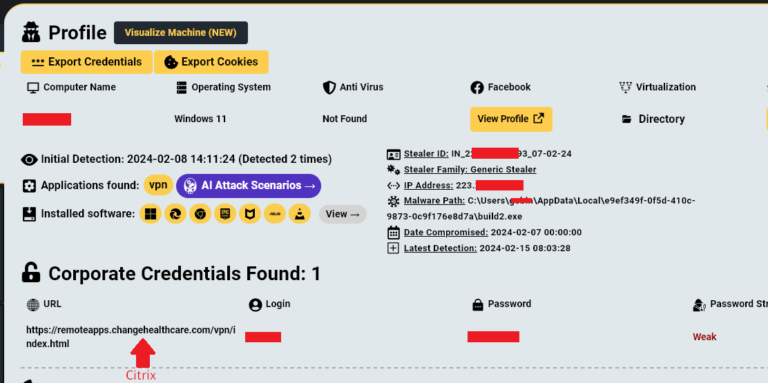
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000

By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting

By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail

By [Alon Gal] | March 2025 Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs. A hacker going by the

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
