The Google 0-day all Infostealer groups are exploiting.
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…
Home » Cybercriminals

Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…

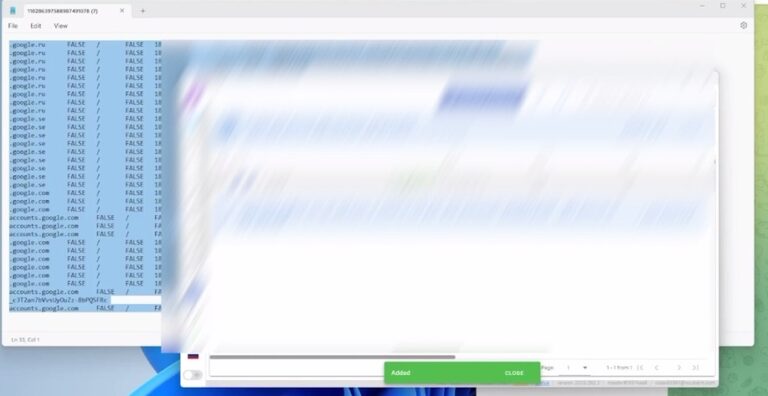
Session cookies are specific web cookies used to allow a browsing session to log in to a website’s services automatically…

The Lumma information-stealing malware is now using an interesting tactic to evade detection by security software…
In a significant development, the creators of the well-known Infostealer group, Lumma, have reportedly made a groundbreaking discovery…

What causes a man to wake up one day and say, “I’m going to build my own malware and go sell it to cybercriminals on the dark web”?

A relatively unknown threat actor who goes by the alias “USDoD” posted a thread in which they offered the database of the FBI’s…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

By [Alon Gal] | April 2025 The HellCat ransomware group has once again demonstrated their relentless focus on exploiting Jira credentials stolen through infostealer malware, targeting

By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail

By [Alon Gal] | March 2025 Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs. A hacker going by the

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
