Mysterious hacker strikes Iran with major cyberattacks against industry leading companies
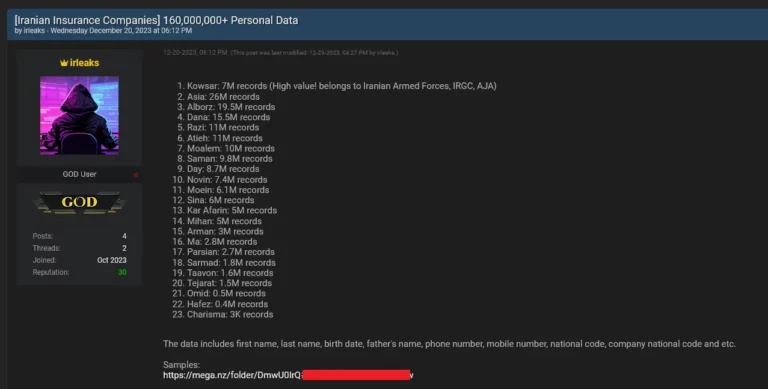
A hacker who goes by the username “irleaks” posted a thread in which they attempt to sell over 160,000,000 records of Iranians…
Home » Hudson Rock » Page 2

A hacker who goes by the username “irleaks” posted a thread in which they attempt to sell over 160,000,000 records of Iranians…
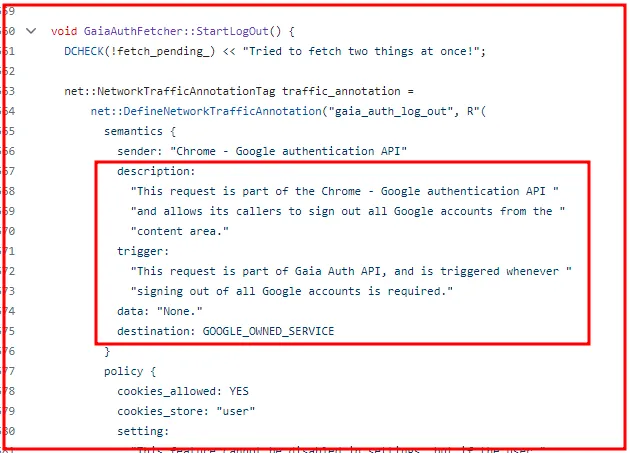
The Lumma Infostealer’s cookie restoration method operates by leveraging a key from restore files, allowing the revival of expired Google cookies…
Today, even despite attempts to alert Google over a month ago that there is an ongoing 0-day being exploited by Infostealer groups…
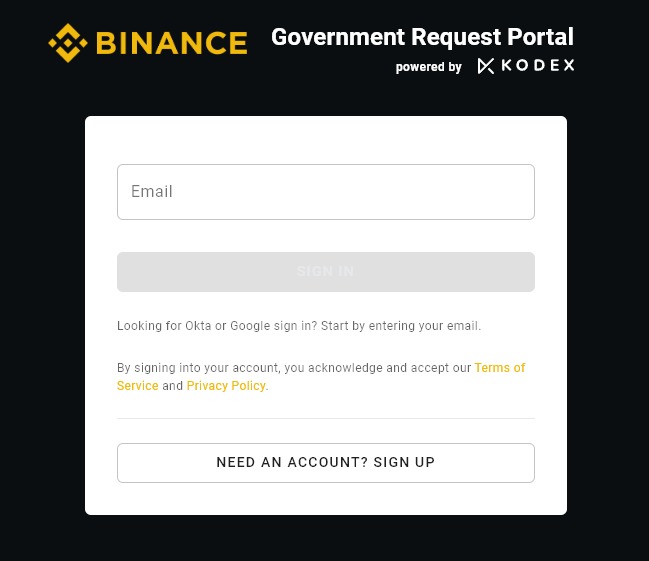
A threat actor attempts to sell access to a sensitive area of Binance — the major cryptocurrency exchange’s…
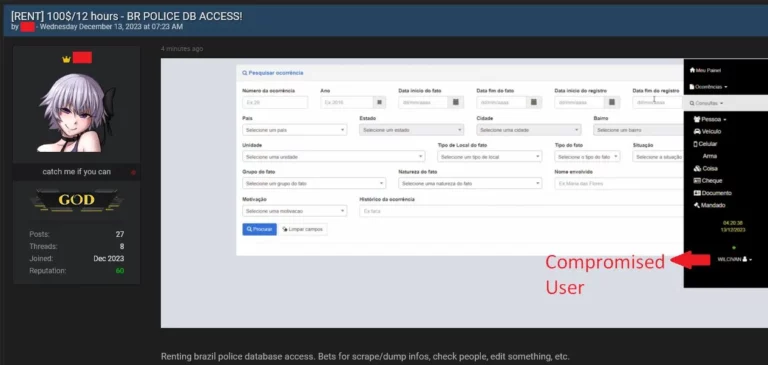
It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks…

Threat actor “La_Citrix” is known for hacking companies and selling access to their citrix/vpn/RDP servers or otherwise for selling info-stealer logs from computer infections…

In this last part of a three part series, our teams summarize the major takeaways from our joint research and provide you with some actionable recommendations…

In this second of a three blog post series, Cyrus and Hudson Rock reveal how the info-stealer threat looks from the hacker’s point of view…

An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data…

By [Alon Gal] | April 2025 Just days after reporting on the Samsung Tickets data breach, another massive leak has surfaced, this time targeting Royal Mail

By [Alon Gal] | March 2025 Another colossal breach fueled by infostealer malware, and this time, it’s Samsung in the crosshairs. A hacker going by the

By [Alon Gal] | March 2025 StreamElements, a popular cloud-based streaming platform, has confirmed a significant data breach involving a third-party service provider, following reports of

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
