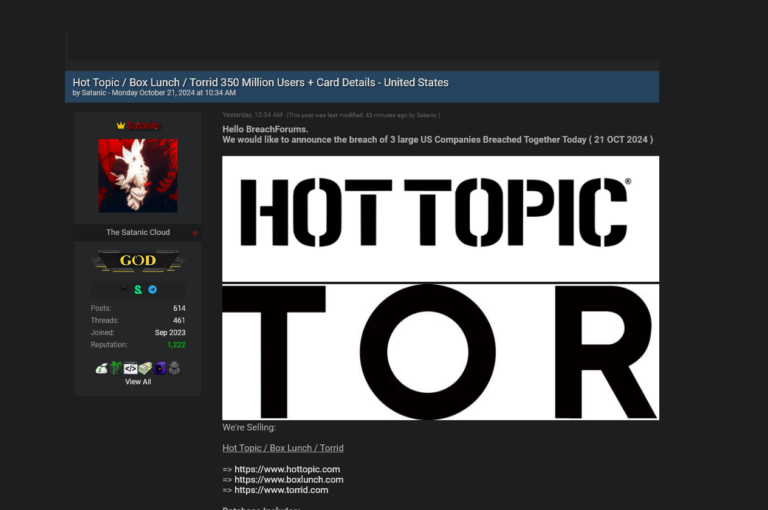
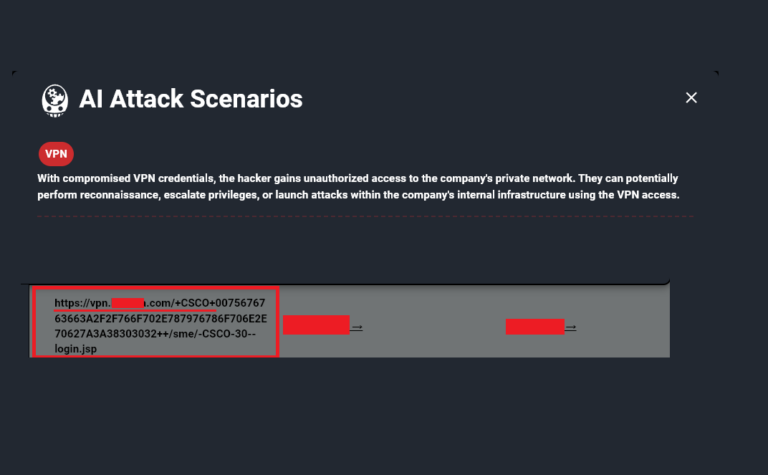
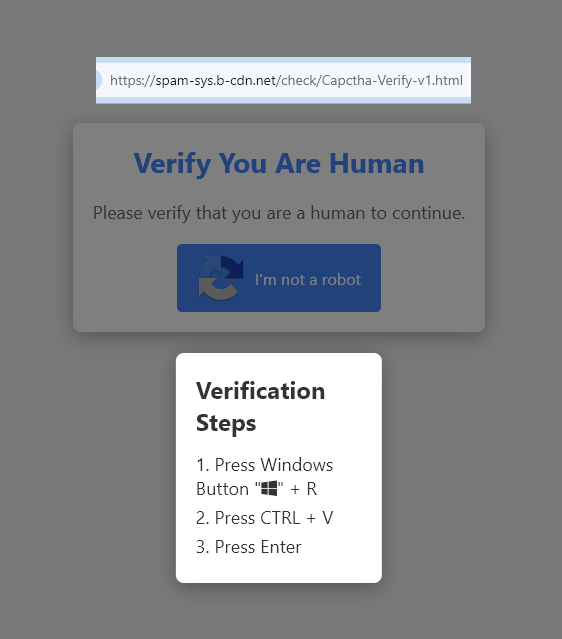
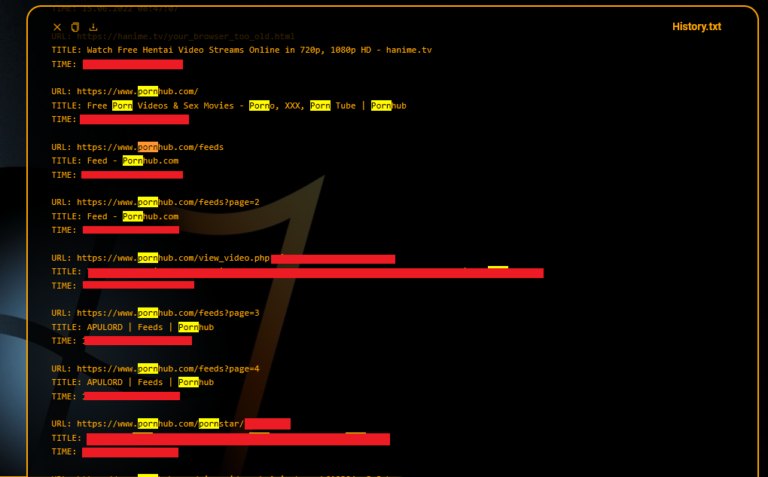
Threat actors use copyright infringement phishing lure to deploy infostealers
Phishing email campaign targets Taiwan Talos observed an unknown threat actor conducting a malicious phishing campaign targeting victims in Taiwan since at least July 2024.