
Key Learnings from Files Present on the C2 Server of an Infamous Infostealer Malware
This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
Home » Infostealers » Page 3

This method can be applied to multiple other C2 servers that we come across on a daily basis to check for any security misconfigurations…
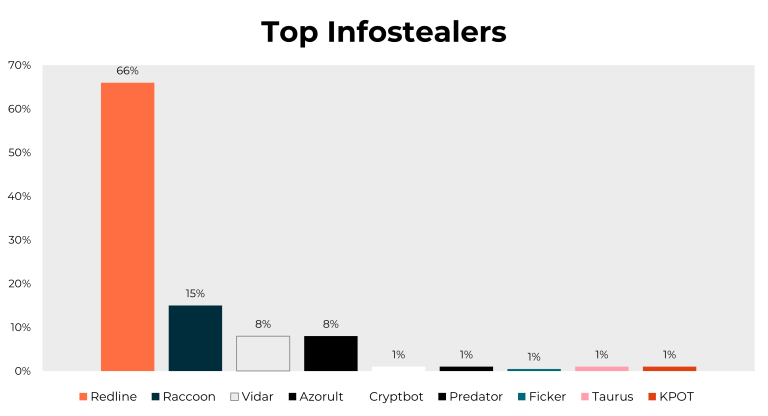
Infostealers are a type of malware designed to steal information from the victim system in order to send it to the attacker…
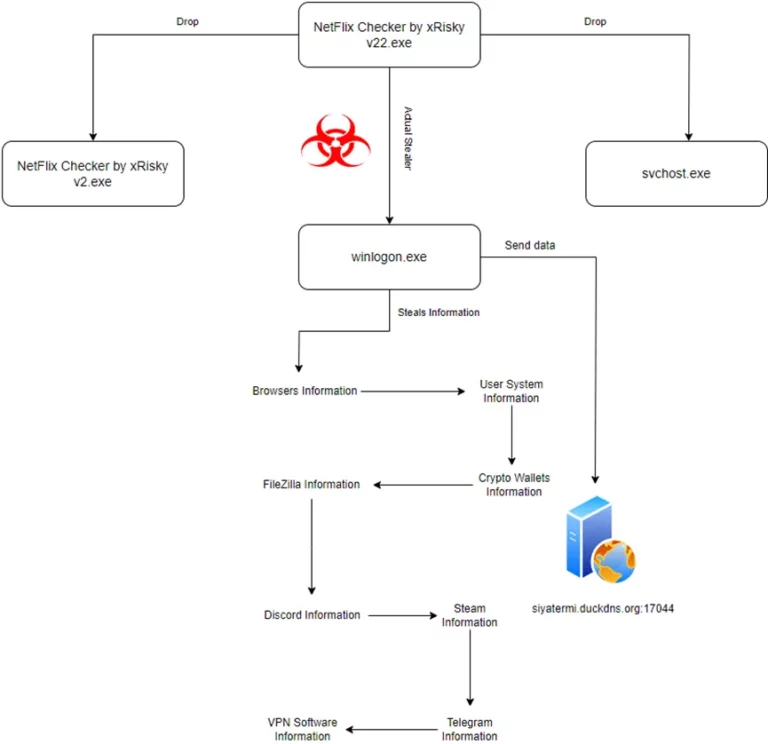
RedLine Stealer is a dangerous type of malware that can cause serious harm to both individuals and organizations…
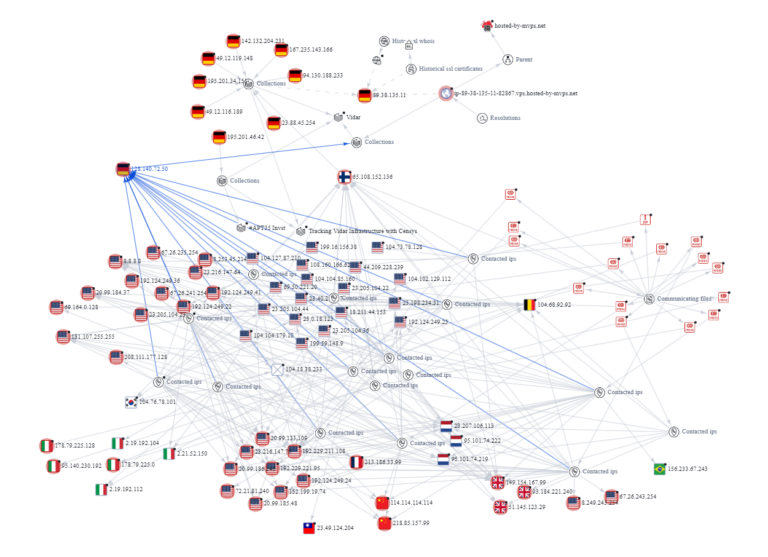
Vidar steals information including login credentials, browser history, cookies and other data and sends it all back to the operator…

Installation of Epsilon infostealer enabled exfiltration of browser-stored data, including passwords, credit cards, and cookies and more…

The threat landscape meets a new player – Rugmi Loader. This threat specializes in spreading spyware, and is in fact capable of delivering any malware type…

Pure Logs Stealer first appeared on hacking forums at the end of October 2022. The stealer is developed by a malware developer…

During the summer of 2023, cyberattacks rose significantly, according to data from the new quarterly BlackBerry Global Threat Intelligence Report, November 2023 edition…

Windows and macOS systems have been subjected to attacks leveraging the novel Go-based information-stealing malware JaskaGO, reports The Hacker News…
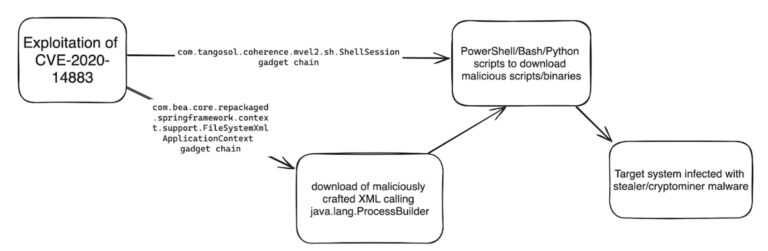
The 8220 gang has been leveraging an old Oracle WebLogic Server vulnerability (CVE-2020-14883) to distribute malware, the Imperva Threat Research team has found…
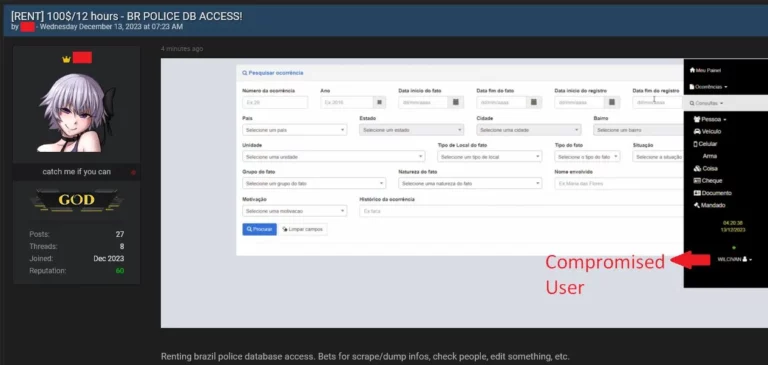
It is not uncommon for threat actors to exploit login data obtained from Infostealer infections to carry out various types of cyberattacks…
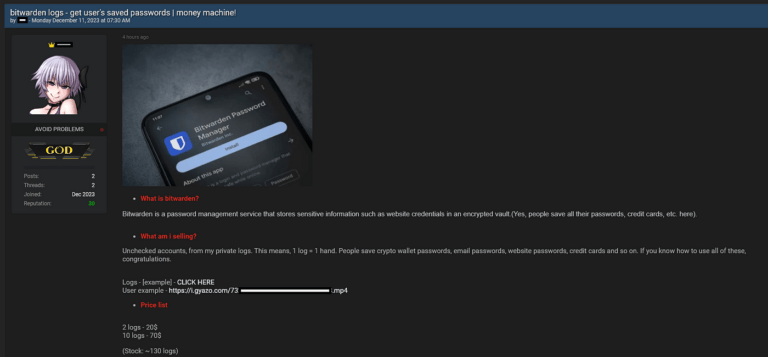
In today’s digital landscape, the reliance on password managers has become commonplace, providing users with a sense of security…

By [Alon Gal] | March 2025 StreamElements, a popular cloud-based streaming platform, has confirmed a significant data breach involving a third-party service provider, following reports of
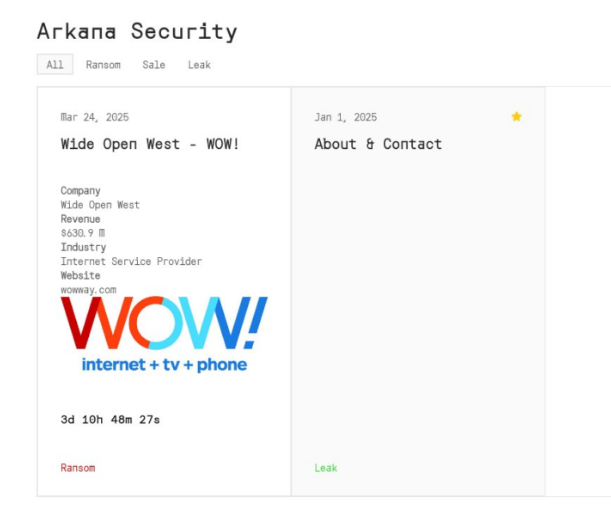
In yet another reminder of the dangers posed by infostealer malware, the emerging Arkana ransomware group has claimed responsibility for a massive breach of WideOpenWest
🔊 *Hudson Rock* is back with a new podcast episode! In this episode, Leonid Rozenberg, cybercrime and threat intelligence researcher, speaks with Kevin Poireault from

Stay informed with the latest insights in our Infostealers weekly report. Explore key findings, trends and data on info-stealing activities.
