
Approaching stealers devs : a brief interview with StealC
STEALC uses a unique log exfiltration by parts on exe builds. This type of communication between build and server panel…

STEALC uses a unique log exfiltration by parts on exe builds. This type of communication between build and server panel…
Amadey is a malware known as a “loader”: its main functionality is to load other payloads for all or specifically targeted computers…

Vidar is one of the top 5 stealers in the market but their users are doing a good job hiding their activity…

Meduza is one of the youngest malware projects that I’ve seen on the market. It is kind of active at the moment…

Session cookies are specific web cookies used to allow a browsing session to log in to a website’s services automatically…

The Lumma information-stealing malware is now using an interesting tactic to evade detection by security software…

It is a fact that the use of Lumma has been increasing a lot: some people participating actively in the market…

Recent weeks have seen a number of macOS-specific infostealers appear for sale in crimeware forums…

What causes a man to wake up one day and say, “I’m going to build my own malware and go sell it to cybercriminals on the dark web”?

An information stealer is a type of malware that gathers sensitive information stored on a device. Once a computer has been infected, the info-stealer uses various techniques to acquire data…
🚀 Big News for Recon & OSINT Professionals! 🚀 🤝 We are thrilled to announce that Hudson Rock is now officially integrated with theHarvester, one
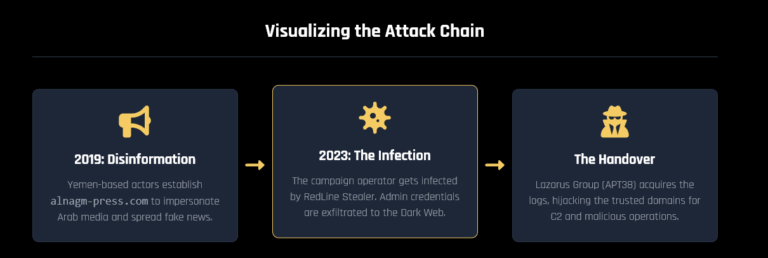
Hudson Rock Report: The Infostealer to APT Pipeline HUDSON ROCK Cybercrime Intelligence Back to Home APT Threat Intel Disinformation The Infostealer to APT Pipeline: How
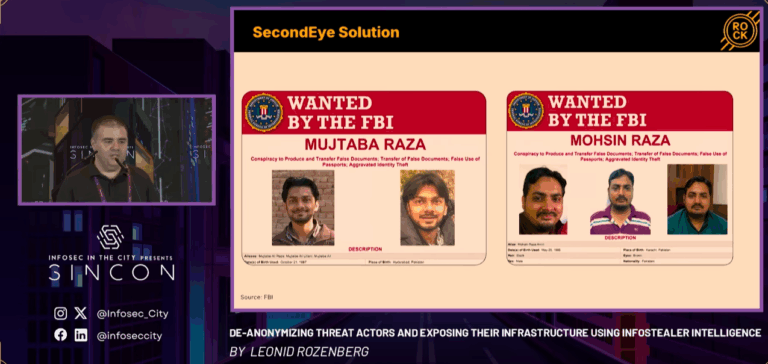
Speaker: Leonid Rozenberg, Cybercrime Researcher, Hudson Rock. Infostealing malware has become a near-perfect tool for cybercriminals, enabling the theft of sensitive data with remarkable efficiency.
